Contingency plans are those whose outcomes are not prepared for. Hence a contingency plan keeps an organization step ahead for disaster management. The disaster could be both man-made and environmental and creates security holes in the organization (Vacca, 2013). Hence this report aims to identify the information security contingencies for helping various organizations.
The report contains the security contingencies that have been defined by the NSW government. The diagram for understanding the contingencies have been developed with the help of Visio. Further, detailed information about the description, with the identification of the various risk exposure has been done. Finally deliberations regarding the ranking have been given, and approaches of NSW government for risk control and mitigation has been evaluated.
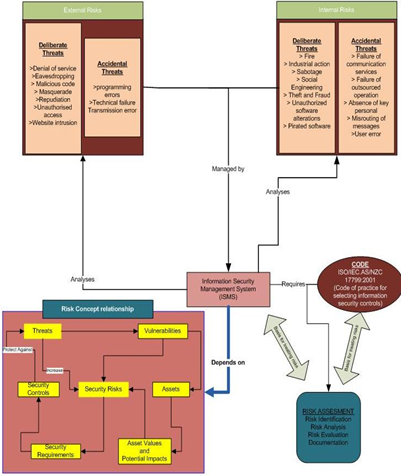
Figure 1: Security contingencies defined by NSW government
(Source: Created by author)
The above diagram shows the various factors and concerns that are considered as Information and security risk by NSW government. As per the illustration, the various internal and the external risk factor has been classified as deliberate and accidental threats components. The deliberate threats are willful damage and manipulation of data whereas accidental threats are random in nature and are hard to predict (Digital Information Security Policy | NSW ICT STRATEGY, 2016). The risk concept relationship shows the interdependence of the various security components regarding security risk and control. Information and security management system (ISMS) should be capable of analyzing threats efficiently hence its development is primarily concerned with the risk concept relationship. The risk concept link acts as the guideline for the formulation of both Code and ISMS and serves as the guideline for mitigation of security risks for NSW government (NSW Government Digital Information Security Policy | NSW ICT STRATEGY, 2016).
Internal Risks are the threats that arise due to the internal factors like the employee of the organization or organizational policies. From the illustration, the various deliberate and the accidental threats that have been identified are classified into four segments (Pedersen, 2013). Thefts, Industrial action, failure of communication, fraud, failure of outsourced operation are treated as a high threat as any of the contingencies will cripple the system (Wehbi Oca & Bourdelles, 2012). Social engineering and absence of valuable personnel have been given medium risk priority (Peltier, 2016). Unauthorized software changes, fire, misrouting of information are of medium-low risk, and low-risk factor has been allotted to sabotage piracy and errors committed by employees as they have low possibilities of happening.
External risks result due to the factors that work outside the organizational aspect. These threats could be a result of persons trying to defame the organization or gain data to be ahead in the race. External accidental threats to contribute to the failure of the system. The high-security threats that can cripple the system are the denial of service, eavesdropping, unauthorized access and software programming errors (Ward & Peppard, 2016). Malicious codes to cripple the system, destruction of data and technical failure are considered as medium level threats. Masquerade and repudiation are considered as medium-low level threats, and the low-level threats are unauthorized access, website intrusion and transmission error (Peltier, 2016).
Various organizations around the world have different codes and security management systems for ensuring data security of their organization. These security measures are targeted against both external and internal risks. The information security guideline formulated by NSW government gives a framework for threat reduction and mitigation for commercial risks (Peltier, 2016). Since the threats are evolving continuously in ICT (Information and communication technology), the security measures should be made stricter. Hence the NSW government faced a lot of challenges regarding accessibility and reliability.
Deliberate threats can be understood as willful wrecking and manipulation of data by a human factor. The damage can be done both to hardware and software. The malicious human intent is the key to deliberate attacks. As stated Nassimbeni, Sartor and Dus (2012), most of the deliberate attacks are targeted at the websites of various organizations for stealing personal and financial data. There are few instances where companies were attacked for denial of services. Denial of services attack needs lesser expertise but is capable of creating chaos. Such attacks reduce the business and credibility of the organization (Wehbi Oca & Bourdelles, 2012). Deliberate attacks include viruses, Trojan horses, malware, spyware, worm, phishing, keylogger, etc. (Tsalis, 2015). These attacks result in financial and confidentiality loss, loss of capability of organizations and can be a threat to life too. These attacks can be done through various means like pen drives emails etc.
The accidental threats are random in nature and can be due to both environmental and human factors. These threats could be the result of an omission or an error. Accidental threats may be the resultant of sabotage but are most likely to be random errors or omissions (Burdon, Siganto & Coles-Kemp, 2016). The accidental threats can lead to an extensive loss like financial, confidentiality and disruption of services. Disruption of communication is the most common form of accidental threats which can be the result of natural calamity. Also, programming errors due to users can result in corruption of information and data, which cannot be retrieved quickly, has been considered as a significant threat by NSW government.
Analysis of the various threats that have occurred in various organizations, it was observed that among deliberate, accidental and environmental threats, deliberate threats are most compromising compared to others (Klaic & Golub, 2013). However, the other threats are real and need to be addressed with due consideration. The table below shows the ranking of the threats
|
Threats |
Impact |
Ranking |
|
Deliberate Threats |
The detailed analysis on the topic shows that the threats that are most compromising are deliberate in nature. The factors like theft, fraud, masquerade, DOS, industrial action, etc. are all present under this umbrella and are known to create a maximum impact upon availability, accountability, reliability and authenticity of an organization, hence making it most dangerous. |
Very high |
|
Environmental Threat |
In this concern, most of the actors that result in defamation of a company are absent apart from reliability and accountability. These threats result in loss of services and impact is pretty moderate (Burdon, Siganto & Coles-Kemp, 2016). |
High |
|
Accidental Threats |
Confidentiality and integrity of an organization are compromised in this security concern, but availability and reliability are not compromised hence making are less risky compared to other threats. |
Low |
It can be seen from the above table that the highest threat ranking has been given to deliberate risk. This has been done because the threat compromises with data privacy and security (Nassimbeni Sartor & Dus, 2012). Such attacks can compromise every information available and needs not authorization for misusing it. This threat has highly affected NSW government and hence has been given the highest rank. A recent report on ‘The Huffington Post’ discusses the same issue regarding the safety from hacking and cyber attacks (Pedersen, 2013). The report emphasizes the need for better security and practices to stop such attacks. An incident of website hacking that has defamed an organization can be seen in the report of ‘Daily Mail’ which discusses the particulars regarding the divorce of a client resulted due to the leaking of data about the client of ‘Ashley Madison’ (Dailymail.co.uk, 2016). Such news is a live example of the importance of information that is contained in a website and how these data can affect user's life.
Accidental threats are a result of errors created by human and are very rare compared to other risks. Since the risks are very rare, and the impact upon the organization is low most of the times. Hence the threats are given low priority (Nassimbeni, Sartor & Dus, 2012). The similar accident that exposed the ‘golden keys’ that unlocks the secure Windows devices was reported in a report in ‘Tech Times’ (Techtimes.com, 2016). Although no names were mentioned the report clearly states the mistake was done. Such accidental leaks give a hacker an additional edge over the inbuilt security, and hence should be prevented. One more similar incident regarding accidental exposure of driver detail of Uber shows that accidental security risk exposure is not uncommon (McCormick, 2015). The accident exposed the personal details of all drivers including the taxi certification forms and driving licenses.
The NSW government faces various challenges regarding the security of information systems (NSW Government Digital Information Security Policy | NSW ICT STRATEGY, 2016). The issues faced by ICT are:
Community for information security, are the various security communities adopted by the NSW government to mitigate the issues related to information systems (Peltier, 2016). These systems or communities are responsible for implementation of formulated policies within the system and in different regimes.
Communication of events and incidents allows the dissemination of information about the various issues to other communities (Wehbi Oca & Bourdelles, 2012). This allows other communities, and NSW government to be well prepared for the contingencies.
Integrity within the system is another issue related to NSW government for standardizing information system security policies (Wang & Lu, 2013). Integrity in the system allows authentication of different parameters related to the system and creation of team which constantly manages the security issues in the system.
Risk and uncertainty play an important role in controlling the contingencies. The NSW government has considered the following difference for the same.
|
|
Risks |
Uncertainty |
|
Meaning |
It is referred to the probability of losing or the contingencies from the perspective of information systems security. |
These are the contingencies that are unknown and can’t be predicted. |
|
Contingencies |
Known |
Unknown |
|
Controllability |
Can be controlled |
Cannot be controlled |
|
Event Probability |
Can be assigned |
Cannot be assigned |
|
Contingency control |
|
|
The NSW government has evaluated various approaches for control and management of several risks and threats. The framework can be broadly classified into following segments (NSW Government Digital Information Security Policy | NSW ICT STRATEGY, 2016).
Sensitivity evaluation is the process by which the impact of various parameters of security issues on the system is evaluated (Damodaran, 2016). The analysis is used for appraisal and feasibility to combat the security issues that has occurred in NSW government. Sensitivity analysis also allow to understanding the threats that comes through information technology and the way of mitigating the threats in proper way.
Scenario analysis is applied to for economic appraisal and study of the feasibility that is incorporated for mitigation of safety issues for controlling the risks in the system. Moreover, Burdon, Siganto and Coles-Kemp (2016) argued that scenario analysis helps in understanding the purpose of the NSW government and find out the policy in relation to information security.
Review of decision is done to analyze the decisions taken by the organization employees that might risk the security (Klaic & Golub, 2013). Hence this analysis allows only the appropriate decisions to overcome management oriented risks.
Failure modes evaluate the impact of failure upon the system. This approach analyses mode of failure, budget risks created due to various contingencies (Singh & Viswanadham, 2012). To overcome such contingencies faulty tree analysis and risk survey approach is evaluated in NSW government.
The aim of the report was to illustrate the current security risks and concerns that have been identified by NSW government. Hence for the analysis, a detailed diagram has been constructed with the help of Visio. The diagram was deliberated and the high, medium, medium-low, and low-risk components were identified. Intentional, environmental and accidental threats were discussed and were ranked for a better understanding of the threats that linger upon the industries. Finally, the mitigation approaches available with NSW has been reviewed and evaluated. Comparative analysis of risk and uncertainty was done, and finally, evaluations of different approaches available with NSW government have been done to mitigate the threats.
Dailymail.co.uk. (2016). Scorned wife launches first Ashley Madison divorce case Mail Online. Retrieved 19 August 2016, from https://www.dailymail.co.uk/news/article-3205657/Wife-starts-Ashley-Madison-divorce-proceedings-husband-outed-member-infidelity-website.html
Damodaran, A. (2016). Damodaran on Valuation: Security Analysis for Investment and Corporate Finance (Vol. 324). John Wiley & Sons.
Digital Information Security Policy | NSW ICT STRATEGY. (2016). Finance.nsw.gov.au. Retrieved 16 August 2016, from https://www.finance.nsw.gov.au/ict/priorities/managing-information-better-services/information-security
Klaic, A., & Golub, M. (2013). Conceptual modeling of information systems within the information security policies. J Econ Bus Manage, 1(4), 371-376.
McCormick, R. (2015). Theverge.com. Retrieved 19 August 2016, from https://www.theverge.com/2015/10/14/9529095/uber-leaks-personal-information-hundreds-drivers
Nassimbeni, G., Sartor, M., & Dus, D. (2012). Security risks in service offshoring and outsourcing. Industrial Management & Data Systems, 112(3), 405-440.
NSW Government Digital Information Security Policy | NSW ICT STRATEGY. (2016). Finance.nsw.gov.au. Retrieved 16 August 2016, from https://www.finance.nsw.gov.au/ict/resources/nsw-government-digital-information-security-policy
Pedersen, C., (2013). The Rising Digital Missile Gap: The Security Threat of the United States' Cyber Inactivity. Pepperdine Policy Review, 6, p.K1.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: Guidelines for effective information security management. CRC Press.
Singh, P., & Viswanadham, P. (2012). Failure modes and mechanisms in electronic packages. Springer Science & Business Media.
Techtimes.com, (2016). Microsoft Accidentally Leaks 'Golden Keys' That Unlock Secure Boot-Protected Windows Devices: Oops?. Retrieved 19 August 2016, from https://www.techtimes.com/articles/173282/20160811/microsoft-accidentally-leaks-golden-keys-that-unlock-secure-boot-protected-windows-devices-oops.htm
Tsalis, N. (2015). Online security or insecurity: The current threat landscape.
Vacca, J. R. (Ed.). (2013). Managing information security. Elsevier.
Wang, W., & Lu, Z. (2013). Cyber Security in the Smart Grid: Survey and challenges. Computer Networks, 57(5), 1344-1371.
Ward, J., & Peppard, J. (2016). The Strategic Management of Information Systems: Building a Digital Strategy. John Wiley & Sons.
Wehbi, B., de Oca, E. M., & Bourdelles, M. (2012, April). Events-based security monitoring using MMT Tool. In 2012 IEEE Fifth International Conference on Software Testing, Verification and Validation (pp. 860-863). IEEE.
To export a reference to this article please select a referencing stye below:
My Assignment Help. (2017). Information Technology Risk Management: Contingency Plans Essay.. Retrieved from https://myassignmenthelp.com/free-samples/information-technology-risk-management-contingency-plans.
"Information Technology Risk Management: Contingency Plans Essay.." My Assignment Help, 2017, https://myassignmenthelp.com/free-samples/information-technology-risk-management-contingency-plans.
My Assignment Help (2017) Information Technology Risk Management: Contingency Plans Essay. [Online]. Available from: https://myassignmenthelp.com/free-samples/information-technology-risk-management-contingency-plans
[Accessed 31 May 2025].
My Assignment Help. 'Information Technology Risk Management: Contingency Plans Essay.' (My Assignment Help, 2017) <https://myassignmenthelp.com/free-samples/information-technology-risk-management-contingency-plans> accessed 31 May 2025.
My Assignment Help. Information Technology Risk Management: Contingency Plans Essay. [Internet]. My Assignment Help. 2017 [cited 31 May 2025]. Available from: https://myassignmenthelp.com/free-samples/information-technology-risk-management-contingency-plans.
