What is Hacking?
Question:
Describe about Hacking, Different types of Hacking Attacks and Computer Hackers and Predators?
This research reflects the types and methodology of Hacking. Hacking is the most popular computer technology that used to modify other computer setting. This research mainly aims in identifying the threats of information security regarding hacking. Understand the different types of hacking and the ways of protecting hacking. This study demonstrates that several types of hacking available in computer security system such as phishing, worms attack, spoofing, fake websites, etc. In order to defines the different types of hacking attack, researcher segment into three major different parts such as simplicity, mastery and illicitness. In order to understand the affect of hacking, researcher explained properly by differentiating into three part effects on single user, affects on countries and companies. Moreover, major aspects of hacking methodology such as foot-print, scanning, enumeration and post exploitation has been described with examples. After identifying the types and affects of hacking, researcher explained the method of protecting computer from hacker.
According to Mansfield-Devine (2014), hacking is the practice of features modification in computer system. From the Information and Communication technology viewpoint, hacking is the method of breaking computer system. There are several people engaged themselves as a part of hacking and the activities of hacking are their profession. These types of people called professional hacker (Sanger et al. 2013). Now a days, computer hacking is the most common and popular term. In the field of computer security, hacking existed in various norms and forms such as brain hacking, phone hacking, internet hacking, etc. In order to hack other device or computer system, hacker uses different tools like worms, exploits, viruses, etc.
- What are the key threats in computer security from hacker?
- What are ways of protecting computer hacker and predators?
- What are the types of hacking?
- How hacking effect?
Hacking has been classified broadly and divided it into different categories such as –
- Phishing
- Trojan programs
- Spyware
- Worms Attack
- Electronic Bulletined Boards
- Fake Websites
- Spoofing
- Information Brokers
- Internet Public Records
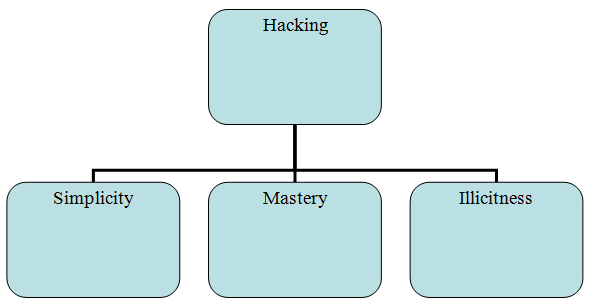
Figure 1: Major Types of Hacking Attack
(Source: Goldstein, 2010, pp- 33)
Spyware: Spyware applications are typically bundle of hidden component that automatically installed into the computer system when users download application from freeware and shareware software. There are various types of people used spyware. There are several common form that used by the attackers such as –
Browse Hijacking – This type of spyware hijack the victim computer’s internet browser setting and modify the behavior of browser. As a result, computer user mostly viewed several advertisements when they visit the site.
Cookies and Web Bugs – Cookies allows the user on storing information or browsing history into the main memory of web browser. When the user lost of forget about a particular website, cookies help in redirecting it. However, Hacking (2010) argued that cookies are mainly used to store authentication, state of information of user and preference. Attacker using the technique of web bug access information of browse and build individual profiles.
Fake Website: Haywood (2011) argued that fake website is the common trade of hacking in these modern days. Hacker using big brand name develop website with little difference such as suny.com instead of sony.com. However, majority of hackers used bank name when they develop fake website and allow user to put information about bank details. This type of website looks same according to the original website.
Types of Hacking Attacks
Phishing: Phishing is the most popular and common attack regarding hacking. This technology is mainly used by the attackers in stealing sensitive information of computer user such as username and password, details of credit and debit card, etc. Trustworthy entity in electronic communication is the appropriate method of phishing attack. Hackers use technology of hacking in order to exploits the sympathy of people via e-mail attacks. Attacker sends e-mail into the personal mail of people where pone website link attached. In major cases is has been seen that attacker attached link of charitable websites or banking or large organization (Gold, 2012). When the attacker open this link it seems to be visit an charitable or banking website but actual Trojan programs run into the system. In order to protect information of computer, user should not link on those types of link (Sanger et al. 2013). In order to safeguards own-self from such kind of attack, computer user has to avoid this link. Leithner & Weippl (2012) argued that the attackers use several techniques of phishing such as –
Manipulation of link – Link manipulation is common and useful technique from the point of view of phishing. Attacker using technical deception creates a link for email that often misspelled such as www.suny.com instead of sony.com. Mortleman (2011) argued that creation of sub domain is the common tricks for hackers. Apart from that, it has been seen that majority of attackers used spoofing technique create a link and allows computer user to put username and password.
Phone Phishing – Recently, phishing through phone increased high. Attacker send message into the mobile devices such as tablets, Smartphone, etc. Attacker told to user as a bank perspective to dial a phone number and giving the bank account details including net banking user id and password (Escalona Vásquez, 2011). Majority of phishing attacker uses fake caller ID data in terms of showing results to user that calling come from trusted organization. Once the phone number dialed by user attackers, it prompts to input the banking id and pin to the users.
Filter Evasion – This is the most recent technique that used by the phishing attacker. Instead of text, most of the phishing attackers uses image that make harder to anti-phishing (Davies, 2010). Filter usually detects the phishing attack in text format but it unable to detect phishing attack in images.
Trojan Programs: This is also a major attack in hacking environment. Attackers first invite into chat room and instantly installed Trojan programs into the victim’s computer. If the Trojan programs installed once in computer, it make difficult to prevent file or sensitive information in computer from attackers.
Sponsors (2010) argued that Trojans are the exactable programs that creates lot of hesitation in system. For example, when the users affected by Trojan attack they cannot perform or handle their computers in proper way like they try to open some files but it opens another file. There are several techniques that used by the attacker in order to install Trojan programs into the computer system. These are as follows –
Spyware
Lookalikes – Hackers sent message to install some files with various types of extension such as exe, vbs, bat, etc. In major cases it has been identified that attacker send Trojan file with some attractable name where two or more extension contains such as looking for girlfriend.txt.vbs or love letter for you.txt.vbs, etc (Dwivedi, 2009). This is the common technique that used by the attackers in terms of installing Trojan program into victim’s computer.
Spoofing: In computer security environment, spoofing is the technology that allows attackers in creating TCP/IP packets using other computer’s IP address. There are various types of spoofing present in computer hacking system such as IP spoofing, Server spoofing, etc.
IP Spoofing – Attacker using the IP spoofing technique directed a specific computer and crash the windows system or look up the system. IP spoofing also allows the attackers in accessing the information in the forms of routing. Therefore, ZOTOS (2011) acknowledged that main attack of IP spoofing is session hijacking where the attacker continuously monitor the session of a personal computer on the network. After complete the authentication, hacker using technology hack client’s computers and crash the system or steal information.
Server Spoofing – It is also a common factor of spoofing over network. Attacker using the technique of C2MYAZZ read username and password of victim computer in the form of sending network packets.
DNS poisoning – Using the spoofing technique, attacker diverted DNS information of client’s computer.
4.1 Single
Single computer hacking indicates the effect of hacking in personal computer system. There are several effect of computer hacking that create variety of damage in the system. Identity theft is the major terms in computer hacking, apart from that website security, email access are also the effect of computer hacking (Annachhatre et al. 2014). Following are the effect of hacking that faced by the single user –
Damage to information – Hacker using the tools and techniques such as installing Trojan program into computer, including bad cookies like web bugs, sending phishing emails link, etc damage the information of steal information from a personal computer. Michael (2012) argued that personal computer user never activated their firewall security in terms of preventing unauthentic access by third party. Apart from that, most of single user never installed antivirus software in their computer system. Hacker takes advantage of these types of lack of scarcity of the single computer user and easily access information or crashes the system of personal computer (Sanger et al. 2013). Zombie attack is the popular and common threat of damaging personal computer or stealing information from the computer.
Theft of information – In these modern days, people would like to shows their activity over internet such as purchasing of products, bank account open online, application for identity card online, demand for credit card online due to lack of available time. Mansfield-Devine (2009) cited that time is the major issues in these busy schedule days. However, due to digitalized the system, bankers send account related information such as account number, credit card number, user id and password of credit card, etc via email. Hacker takes advantage of digitalization. Using several types of fraud techniques like phishing attack allows to put username and password in a fake link and access information of the user (Beaver, 2010). Moreover, it has been often seen that, hacker using hacking method crack the system of personal account over network such as personal email id, social network profiles, etc and input wring information or handle with their own way.
Fake Website
In the digital age, companies in business environment or the governmental sector faces lot of challenges regarding hacking. Due to hacking, majority of companies is not able to maintain their interconnected costs properly. In business sector, hacking mainly identified in baking industry.
Theft of identity is the key form of single user from the point of view of hacking. In business, there have several information including confidential accounts, credit card details, debit card details, transaction details (Wallace et al. 2013). Majority of business organization stores their financial information into the network of computer system. Apart from that, in computer file, they stored data or information about employees, social security number, health care information, home address, etc. Hacker of the computer is using several technologies like worms attack, phishing, Trojan program, etc to access information from computer database. Mcfedries (2009) argued that access of sensitive information in unauthentic way is the process of identity theft. It may too much harmful for the business as well as employees along with customers.
On the other hand, Schneider (2010) cited that hacker not only access information in unauthentic way from the victim computer in form of hard drive and website but also access sensitive as well as confidential information via email. As opined by Stryker (2012), email hacking is also an integral part of hacking that create huge trouble to the user. Hacker can access information from email of employees or customers using techniques and access sensitive data such as transaction report, purchased of products, etc. Through malicious attack, hacker access information or sensitive data from personal email of computer user.
Furthermore, website security is also an important part of hacking in companies and governmental sector. In these modern days, in order to sale products directly to customers or increasing brand image largely, organization in both sector private and government developed e-commerce website of their own.
Due to digitalization of business and integration of websites in business process, they become the victim of hackers (Bradbury, 2010). Usually hackers used hacking techniques to steal data from website database and after accessing information destroyed data (Hacking et al. 2013). Majority of organization involve third party vendor in order to develop the websites and maintain it. This can leads high security risk and unable to implement data back function in server. Therefore, due to high risk of data lost into central hard disk storage, majority of organization recently use storage space in cloud using the technique of cloud computing. Simpson (2012) argued that this technique pose high risk for the companies or governmental sector from the point of view of payment related information. Hacker used 512-bit decryption techniques in order to decrypt information of transaction process of the company. Small business organization due to lack of financial resource commonly used 256 encryption technique. Therefore, 512-bit decryption technology easily decrypts the information. Enterprise system security study of 2010 stated that due to hacking attack companies in business sector lost $2.2 million average in their business.
Hacking has potential effect in countries or cities. For example, majority of government stored information in network server in terms of using their own purpose. However, if the professional hackers steal this information and use publicly, it may create more complexity for that particular country.
Phishing
Wiles et al. (2012) argued that we are living in the society of information technology. The entire operations or daily activities of people in these days are controlled by the technology. From this point of view, if the system broken or hacked by third party it will be great damage. Government of developed countries as if USA, Australia, Netherlands, etc design their overall system based on information technology (Coleman, 2013). Due to digitalization, chances of attack or hack information increased highly. Hacker or attacker has great chance to collapse the system of bankers or militaries by breaking down the main system of countries.
Schulz (2010) cited that it would be vital damage in respect to country’s security. As stated by McClure et al. (2009), the country North Korea officially provided training to more than 600 people to be hacker. In the training period, trainer provides information about how to hack the computer system. Thus, North Korea try to begin the cyber attacks against Japan, South Korea, United State, Canada, etc for gathering military intelligences. Mischel (2009) acknowledged that this type of attack are mainly occur to access information from computer system about the vital information such as transaction process of bankers, intelligence of militaries, strategies for growth of economy as well as countries, decision making regarding the policies of foreign countries, etc. On country make policies regarding foreign countries and develop strategies after long analysis (Benford, 2009).
Therefore, stealing of this information may serious harmful for the countries. Apart from that, due to cybercrime countries or cities has to maintain high security regarding their sensitive and credential information. According to the research report of Koch (2010), agents of FBI of the country United Kingdom downloaded information from computer system of Russia. It has been also described on that research report this hacking was done in order to track information and investigate those information on breaking bank networks and internet crimes. However, this approach created lot of controversy.
Foot-printing
In these days, internet has become an integral part of life in both business as well as individuals. Footprint is one of the most popular technique that used by the hacker in terms of gain information. Earlier, hacker has to spend much time in gathering information before hacking the computer system or sensitive data. The process and technique of foot-printing provides critical steps that subvert computer system security for a target system. Foot- printing is the technology that equivalent to potential robbery named casing. Mcfedries (2010) argued that systematic foot-printing allows the hacker in gather wide range of information in terms of creating target system’s profile including IP address, network, domain, internet, intranet, architecture, etc.
Starkman et al. (2012) presumed that foot-printing is the process of analysis target computer system in environment of hacking. Through tools and techniques of foot-printing, hacker is able to identify, analysis and discover information about the target computer system. Wright (2011) argued that majority of hackers used this tools because it is the open source tools. According to Sinchak (2004), foot-printing is widely used ad most beneficial for trace routes, network lookup, web search hacking, etc. Foot-printing allows the hacker in gleaning information about target computer system and break the barrier of limit of information.
Trojan Programs
As argued by the Murphy (2011), scanning is an integral part of hacking methodology from the point of view of storing information from foot-printing. However, McClure et al. (2012) suggested that scanning drill down the findings a bit further. Scanning is mainly used in hacking for scanning of port, packets, identification of operating system, determination of operating system, access of mechanism, etc. Kramer (2012) opined that port scanning is the common used technique of scanning by the hacker. This technique scans User Diagram Protocol (UDP) and Transmission Control Protocol (TCP) of target system. Apart from that, Hancocks (2011) explained there are various types of port scanner available on the internet such as NMAP (Networked Messaging Application Protocol) that helps in mapping the network with powerful ways and make a easy process for hacker in terms of generating flexible information from target computer system. Moreover, there are different tools of scanning except NMAP such as Unicornscan, Superscan, Portscan 2000, etc.
Enumeration is the process of determining exact information about target computer system such as exact operating system of target computer, used software and specific service of target computer, etc. Hacker used normal enumeration techniques such as sharing of information, details about user accounts, SNMP traffic, application running, specific version of running application, etc. Through the enumeration process, hackers are able to track the system information about target victim and properly analyzed the system build a profile for target computer.
This is the hard step as well as most complicated step regarding hacking. This step mainly depends on the objective of mission. Hacking (2009) noted that in order to hack target computer system, hackers have to include mixed up combination of various approach such as data collection, root kit, remote forensics analysis and target survey, computer network attack, etc. In order to be professional hacker and hack the system, attackers have to collect data about target system such as specific architecture, computer operation system, software, etc. Using the tools of rootkit like persistence, aka backdoor, implant, etc, hacker has to build a clear profile of target computer system (Gilman, 2009). Remote forensics analysis and target survey required for hacking the system because before hacking the system survey over target computer is essential in order to know the using purpose of target computer.
The intentionally access of the computer without the authorization and the permission of the users and to work with the user’s personal data and also the modification of computer’s hardware and software is known as computer hacking (Voss, 2006). The persons who are engaged with this type of unauthorized access of the computer are known as hackers. Computer hackers and predators are mostly used to break the systems with the motive to steal, change and destroy the computer’s vital information and infrastructure through the internet facility.
Hacking can also be categorized through different ways. Some of them are given bellow:
Phishing – Phishing is the technique that is most common in hacking. It acts trustworthy website and comes to know all the personal data regarding user name, password and many other details.
Spoofing - Spoofing is another method in which intruders use other’s IP address to create the TCP/IP packets.
Spyware – The bundle of hidden component which are installed automatic into the computer system when any applications are downloaded from the freeware and shareware software.
Trojan Program – Trojan attack is one of the most powerful attacks in hacking. It is a malware program which has malicious code and also instantly installed into the computer and once it installed it is tough to prevent the computer.
Fake website - Fake website is also one of the most common hacking methods of now days. In this, hackers use big brand name to develop the fake website with minute difference so that they can easily get user’s important information.
6.2.1 Use of a 2-way firewall:
Two-way firewall is having all the features of the one-way firewall and protects the host to access anything from outside of campus. For an instance if we have to connect a remote server for any update, the two-way firewall seeks permission whether to allow the application to connect to the server for the safety reasons. Two-way firewall also have some of the characteristics of port cloaking, which have some kind of stealth mode where the computer is not easily detected from outside (Richet, 2013) . So now a days firewall not only protect the user from outside but also secure the information which are going out from the user’s computer.
6.2.2 Refurbish the operating system:
Refurbishing of the operating system describes that the PC, which is used previously, that has undergone through some of the following processes, which helps the new users ready for use. Refurbishing includes three major steps. First of all is data wiping - Data wiping or disk wiping or secure erase procedure is the procedure to delete some of the data due to some of the reasons (Kang, Park & Kim, 2013), Secondly is testing – Testing of the hardware or software includes the testing occurs on the complete, integrated system to determine the system’s affectivity with the specific requirements and at last or thirdly is Cosmetic repair / replacement of defective PC components. If in some cases the installation of the new motherboard occurs then the PC is not known as ‘refurbished PC’ it results to the ‘new PC’.
6.2.3 Increase the browser security setting:
Web browser is the bridge connection of the computer to the rest of the internet. Browser security setting protect the users what they browse on the web. It also restricts to open any of the effected web pages. For instance in case of the Google chrome we have to follow some of the steps to adjust the settings as at first we have to open the chrome menu from the toolbar, then go to settings and from settings select advanced settings and from there we have to adjust as per our requirement ('Browser attacks “can wipe out almost anything”', 2001).
6.2.4 Ignore questionable websites:
Questionable or suspicious websites are usually common for users who often browse the internet. Many of the times, these websites are source of the malware, frauds and other bad things. These types of websites are actually linked with the other main website it opened automatically with the opening of the other websites.
6.2.5 Formation of safe email protocol:
In order to safe email, Transport Layer Security (TLS) is a protocol, which helps to encrypt, and in delivering the mail securely, it helps to prevent message forgery also known as spoofing between the mails servers. TLS and Secure Sockets Layer (SSL) are the cryptographic protocols that are designed in such a way that helps to provide the communication security on the computer network. So to secure the email there are some of the protocols such as POP, IMAP, SMTP, and MAPI which are very useful ('New secure email protocol promised', 2013) .
In order to become a hacker, first need to learn the basics of hacking such as runs Unix operating system in computer. After that need to write HTML code gradually that build in-depth knowledge. In order to became a professional hacker need to learn about the programming language such as C++, Python, etc. The most important think to become hacker is that user has to think like a hacker (Dhanjani et al. 2009). To be a hacker has to show interest in solving large problems and think creative.
There are lots of code programme such as Python, C++, C, etc that helps in designing useful program to the hacker. Apart from that, in order to hack other’s websites or computer system, hacker has to recognize properly and has to be fighter in nature. Competent will be the best methodology to be a hacker. Before hack other system, need to write open source programme and sale it in website.
8. Conclusion
From the above discussion, it is utilized that hacking is tend of wrong media. Hacker attacks the sensitive information in the form of technology. However, it is also identified that hacker has in depth knowledge about computer technology as well as they have inventive feelings. Moreover, this study displayed that there were wide range of threats ad vulnerabilities present in networks and software of computer system that are going to be most important media of life living in the world. Lock of scarcity and fast pace software development is the key reason of software and network vulnerabilities. Regarding complexity of computer, hackers plays important role. Without hacking, it would not be possible to identify the threats and vulnerabilities of developed software. However, in order to improve security system of computer technology, hacking is the key method.
Reference List
Beaver, K. (2010). Hacking for dummies. Hoboken, NJ: Wiley Pub.
Coleman, E. G. (2013). Coding freedom: The ethics and aesthetics of hacking. Princeton University Press.
Davies, S. (2010). Hacking Timbuktu. Boston [Mass.]: Clarion Books.
Dhanjani, N., Rios, B., & Hardin, B. (2009). Hacking. Beijing: O'Reilly.
Dwivedi, H. (2009). Hacking VoIP. San Francisco: No Starch Press.
Hacking, J. (2012). Photography. Munich: Prestel Publishing.
Kramer, J. (2012). Hacking the Kinect. [New York]: Apress.
McClure, S., Scambray, J., & Kurtz, G. (2009). Hacking exposed 6. New York: McGraw-Hill.
Mischel, M. (2009). ModSecurity 2.5. Birmingham, U.K.: Packt Pub.
Schulz, K. (2010). Hacking Vim 7.2. Birmingham, UK: Packt Pub.
Simpson, M. (2012). Hands-on ethical hacking and network defense. New York: Wadsworth Publishing Co.
Sinchak, S. (2004). Hacking Windows XP. Indianapolis, Ind.: Wiley Pub.
Stryker, C. (2012). Hacking the future. New York: Overlook Duckworth.
Annachhatre, C., Austin, T., & Stamp, M. (2014). Hidden Markov models for malware classification. Journal Of Computer Virology And Hacking Techniques. 014-0215-x
Benford, G. (2009). Hacking the planet. New Scientist, 202(2702), 22.
Bocks, B. (2011). Mit Live-Hacking Kunden sensibilisieren. Bankmagazin, 60(6), 20-21.
Bradbury, D. (2010). Digging up the hacking underground. Infosecurity, 7(5), 14-17.
Escalona Vásquez, E. (2011). El Hacking No Es (Ni Puede Ser) Delito. Revista Chilena De Derecho Informático, 0(4).
Gilman, N. (2009). Hacking goes pro [engineering security]. Engineering & Technology, 4(3), 26-29.
Gold, S. (2012). Hacking on the hoof. Engineering & Technology, 7(3), 80-83.
Goldstein, H. (2010). Hacking for humanity. IEEE Spectr., 47(2), 33-34.
Hacking, B., Wallace, L., Scott, S., Kosmalaâ€ÂAnderson, J., Belkora, J., & McNeill, A. (2013). Testing the feasibility, acceptability and effectiveness of a ‘decision navigation’intervention for early stage prostate cancer patients in Scotland–a randomised controlled trial. Psychoâ€ÂOncology, 22(5), 1017-1024.
Hacking, D. F., Gibson, A. M., Robertson, C., & Doyle, L. W. (2013). Respiratory function at age 8–9 after extremely low birthweight or preterm birth in Victoria in 1997. Pediatric pulmonology, 48(5), 449-455.
Hacking, I. (2009). Humans, aliens & autism. Daedalus, 138(3), 44-59.
Hacking, I. (2010). Darwin: A Life in Poems. Common Knowledge, 16(2), 286-286.
Hancocks, S. (2011). Hacks, hackers and hacking. Br Dent J, 211(2), 51-51.
Haywood, A. (2011). Rewards for Hacking – Good, Bad or Ugly?. Infosecurity, 8(1), 42.
Kang, S., Park, K., & Kim, J. (2013). Cost effective data wiping methods for mobile phone. Multimedia Tools And Applications, 71(2), 643-655.
Koch, C. (2010). A smart vision of brain hacking. Nature, 467(7311), 32-32.
Leithner, M., & Weippl, E. (2012). Low Tech Hacking. Computers & Security, 31(5), 738.
Mansfield-Devine, S. (2009). Google hacking 101. Network Security, 2009(3), 4-6.
Mansfield-Devine, S. (2014). Hacking on an industrial scale. Network Security, 2014(9), 12-16.
McClure, S., Mcclure, S., Scambray, J., & Kurtz, G. (2012). Hacking exposed 7.
Mcfedries, P. (2009). Hacking DNA. IEEE Spectr., 46(10), 23-23.
Mcfedries, P. (2010). Hacking the planet [technically speaking. IEEE Spectr., 47(8), 23-23.
Michael, K. (2012). Hacking: The Next Generation. Computers & Security, 31(6), 799.
Mortleman, J. (2011). Phone Hacking Scandal: Who's Getting the Message?. Infosecurity, 8(6), 36-39.
Murphy, S. (2011). Hacking the system, because he could. New Scientist, 211(2825), 49.
Richet, J. (2013). From Young Hackers to Crackers. International Journal Of Technology And Human Interaction, 9(3), 53-62.
Sanger, D., Barboza, D., & Perlroth, N. (2013). Chinese Army Unit is seen as tied to Hacking against US. The New York Times, 21.
Schneider, D. (2010). Camera hacking [Hands On. IEEE Spectr., 47(12), 18-19.
Sponsors. (2010). Nuclear Physics A, 844(1-4), 2c.
Starkman, D., Hamilton, M., Chittum, R., & Salmon, F. (2012). The best business writing 2012. New York: Columbia University Press.
Voss, D. (2006). COMPUTER SCIENCE: Better Technology via Hacking. Science, 312(5780), 1574c-1574c.
Wiles, J., Gudaitis, T., Jabbusch, J., Rogers, R., & Lowther, S. (2012). Low tech hacking. Waltham, Mass.: Syngress.
Wright, A. (2011). Hacking cars. Commun. ACM, 54(11), 18.
ZOTOS, A. (2011). PRESERVATION TIME AT 6 ± 2C AND 8 ± 2C OF TROUT (SALMO GAIRDNERII) FILLETS SMOKED BY STEAMING WITH LIQUID SMOKE. Journal Of Food Processing And Preservation, 35(4), 533-541.
C.ymcdn.com, (2015). Retrieved 9 February 2015, from https://c.ymcdn.com/sites/www.nibs.org/resource/resmgr/Conference2014/BI20140106_CS_Morris.pdf
Blackhat.com, (2015). Retrieved 9 February 2015, from https://www.blackhat.com/presentations/bh-europe-05/BH_EU_05-Long.pdf
Inventwithpython.com, (2015). Retrieved 9 February 2015, from https://inventwithpython.com/hackingciphers.pdf
Pdf.textfiles.com (2015). Retrieved 9 February 2015, from https://pdf.textfiles.com/security/palmer.pdf
To export a reference to this article please select a referencing stye below:
My Assignment Help. (2016). Understanding Different Types Of Hacking Attacks: An Essay.. Retrieved from https://myassignmenthelp.com/free-samples/research-proposal-of-information-security.
"Understanding Different Types Of Hacking Attacks: An Essay.." My Assignment Help, 2016, https://myassignmenthelp.com/free-samples/research-proposal-of-information-security.
My Assignment Help (2016) Understanding Different Types Of Hacking Attacks: An Essay. [Online]. Available from: https://myassignmenthelp.com/free-samples/research-proposal-of-information-security
[Accessed 23 May 2025].
My Assignment Help. 'Understanding Different Types Of Hacking Attacks: An Essay.' (My Assignment Help, 2016) <https://myassignmenthelp.com/free-samples/research-proposal-of-information-security> accessed 23 May 2025.
My Assignment Help. Understanding Different Types Of Hacking Attacks: An Essay. [Internet]. My Assignment Help. 2016 [cited 23 May 2025]. Available from: https://myassignmenthelp.com/free-samples/research-proposal-of-information-security.
