NSW Government comprises of a number of operations and applications on a daily basis. The stakeholders that are involved with every single application and the system as a whole are internal as well as external in nature. There are a number of potential security risks in front of the NSW Government that may cause low to extremely severe impact on the same.
The document covers the security risks by showcasing them in the form of a diagram and explains each of them in detail. It also covers the challenges that NSW Government may face in implementing the security/risk management policies along with the approach that must be followed to prevent these risks. A comparison between deliberate and accidental threats and risks and uncertainties has also been illustrated in the document.
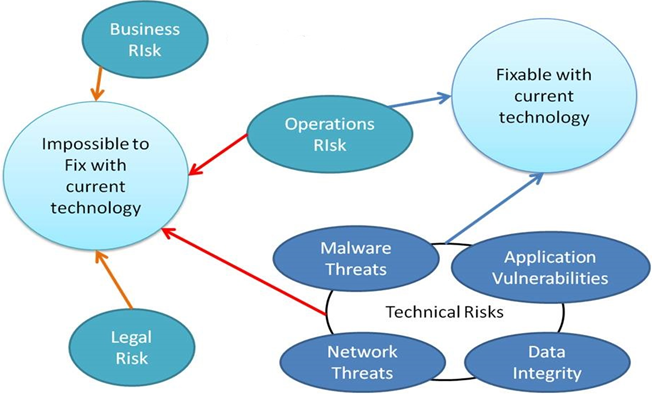
The risks that have been show in the diagram above have got varying degree of severity. The severity of the risks depends upon the type of information that they affect. The information types that are associated with NSW Government are described as follows:
- For Office Use Only
Only the officials that are engaged with the NSW Government are permitted and are authorized to use the information that comes under this category. Access to any one outside the officials will be considered as a security breach.
- Sensitive Information
This information that is present under this category cannot be disclosed under any circumstance without proper authentication and authorization.
- Sensitive: Personal
This is the information that comprises of the personal information of either the user or the fellow organization or agency associated with the NSW Government.
- Sensitive: Legal
With the involvement of a number of internal and external stakeholders and a number of third parties, there is a lot of legal information that is associated with the NSW Government in the form of legal records, policies and many more details.
- Sensitive: Cabinet
This is the information that comprises of the cabinet information such as the policies and decision making documents to enforce a particular policy, other official documents and likewise.
- Sensitive: NSW Cabinet
These are the documents and records that are specifically related to the NSW cabinet such as agendas, policies, laws and associated details.
- Sensitive: NSW Government
NSW Government specific information such as government records, policies, decisions and similar details come under this particular category of information.
- Sensitive: Law Enforcement
There is a lot of information that is associated with the procedure of enforcing a particular law in a specific region or on a wider scale. This is the category of information that is bundled up in this category of information.
- Sensitive: Health Information
The information that is associated with the health of the person is always extremely sensitive in nature and cannot be disclosed without the legal consent of the parties that are involved in a particular piece of information. It may include the medical records of the patient, database of the hospital or other medical agency and likewise.
The risks that are displayed in the security risk diagram can now be explained.
- Data Integrity Risks
Data integrity refers to the confirmation and assurance that the data cannot be modified without authorization and authentication to perform the same.
NSW Government is open to a number of data integrity risks. Apart from the risk to the integrity of the data itself, there are a number of other risks that may afftect the data integrity. Risks in the processing area can easily occur if accurate preventing or detecting measures are not followed. Reporting is another major area that has a huge significance in the case of NSW Government due to the presence of a vast number of entities. There can be violation of integrity in this area that must be controlled. Another major area is the integrity risk in the adopted policy or infrastructure for a required solution.
- Network Threats

The Network threats are further classified in to four types as listed above.
Unstructured Threats: These are the threats that often make use of multiple network systems in order to execute an attack. The system that is attacked and infected is usually not in the knowledge of the perpetrator.
Structured Threats: These threats are executed by the skilled attackers and the target system is detected after a random or specific search process. This type of an attack is mostly backed by the presence of a malicious intent.
Internal Threats: The threats that can be executed on the internal network of NSW Government come under this category of threats.
External Threats: These are the threats that will make use of external networks such as those of the users or third parties (etutorials.org, 2016).
Some of the examples of the potential network threats for NSW Government are:
IP spoofing is a common network threat that may impact the functioning of the applications of NSW Government. In this type of an attack, the attacker first finds out the IP address of the host and then modifies the packet headers to make it appear to the user that the information is coming for the authorized host.
Sniffing is a network threat that works by the process of packet sniffing or monitoring to gain information about the host and the network itself.
Mapping or Eavesdropping is another network threat wherein an attacker acquires the information such as IP address of the system, operating systems and the services.
Man-in-the-middle attack is a network threat in which the attacker sits in between the network of the host and the destination server. All the activities performed are closely monitored by the attacker to acquire useful information (hubpages.com, 2016).
These are the attacks in which the attacker floods the network with unwanted traffic that makes the service unavailable until resolution is made.
- Malware Threats
There are a number of malware that are introduced in the system to affect the functioning of the same. NSW Government and the information that is associated with all of its applications are also exposed to a number of malware threats. These malware are further classified in to further types which can be reproducible and non-reproducible in nature and properties. Viruses, worms, Trojan Horses and Logic Bombs are some of the common malware types (www.us-cert.gov, 2016).
- Application Vulnerabilities
The number of components and applications that are associated with NSW Government and its architecture is massive. The same leads to the presence of a number of application vulnerabilities and threats such as those related to the account hijacking and APIs.
These vulnerabilities can violate the security and privacy of the information that is associated with the system.
- Operations Risks
These are the types of the risks that may result from the inefficiencies of the resources or the machine that is associated with a particular operation.
For instance, poor project management will lead to poor allocation of roles and responsibilities to the associated resources. The skill set of these resources will not be utilized properly and will lead to inadequate results and performance (www.finance.nsw.gov.au, 2016).
- Business Risks
There can be a number of scenarios in terms of internal changes or market trends or other such activity that may slow down the profits associated with the NSW Government. All such possibilities will be covered in this particular category of risks.
- Legal Risks
Violation of any of the legal policy that is associated with NSW Government and the agencies and applications that are associated with it may result in legal penalties and punishment.
Such occurrences may lead to a number of legal risks.
|
Risk ID |
Risk |
Likelihood |
Impact |
Risk Ranking |
|
RS1 |
Data Integrity |
High |
High |
High |
|
RS2 |
Network Threats |
High |
High |
High |
|
RS3 |
Malware Threats |
High |
Medium-Low |
Medium |
|
RS4 |
Application Vulnerabilities |
Medium |
Medium-Low |
Medium |
|
RS5 |
Operations Risks |
Medium |
Medium |
Medium |
|
RS6 |
Business Risks |
Medium |
High |
High |
|
RS7 |
Legal Risks |
Low |
High |
High |
The risks that are associated with NSW Government or any other organization may be intentional or deliberate in nature or may occur by mistake or be accidental in nature. The following table lists out the differences between the two types.
|
Deliberate Risks |
Accidental Risks |
|
These are the threats that may involve either the use of human to human interaction, human to machine interaction or machine to machine interaction for execution and involves the presence of malicious intent behind the same (Vavoulas, 2016). |
There is no malicious intent involved in such types of risks as it occurs by mistake or negligence and are always unintentional in nature. |
|
The impact that is caused by the deliberate threats is often high to severe. |
The impact caused by these threats varies from one threat to the other. It may have a low impact to sever impact as well. |
|
The risks that are associated with the NSW Government include all the malicious threats such as those of viruses, worms, logic bombs and Trojan Horses. Data integrity and network threats are always deliberate in nature. |
There are also accidental threats that are associated with the NSW Government. Application vulnerabilities and business risks are the threats that are often accidental in nature (searchsecurity.techtarget.com, 2016). |
There are also some of the risks that are associated with NSW Government that may be deliberate or accidental in nature depending upon the intent behind the same. For instance, legal risks or the operations risks may occur due to inadequate knowledge or may also be caused by deliberate action.
- Human Factors
There are a lot of human entities involved in the overall functioning of the NSW Government. These include policy makers, end-users, workers, managers, leaders, directors and many others. There are also external resources that are present in the overall architecture. There may be situations wherein there will be scenarios of conflicts and disputes among the two parties. The possibility of the same increases when one of the parties is internal and the other one is external. The same causes delay in the timely implementation of the security/risk management policy. Also, it is essential to have effective communication all throughout to ensure that the correct and timely decisions are made. Failure of the same will lead to hindrance in the implementation process.
- Organizational Factors
There are also a number of organizational factors that may occur in the process of implementation of the security/risk management policy. These factors will include the various levels present in the organization such as top level management, middle level management and many others. It is necessary to have the supreme level of transparency at all the organizational levels to have correct implementation of the security policy.
- Technological Factors
Technology is something that is changing at a continuous pace. The same can emerge as one of the major issues in the successful implementation of the security policy. There may be situations where the existing technology of the NSW Government may not be sufficient or compatible with the recommended security mechanism. There will be changes that will be required to be done in the technological architecture to implement the security features that may cause a delay.
There are a number of risks that are associated with a particular system. There can also be certain events which cannot be predicted in advance but always have a possibility in case of a system or an operation.
A risk refers to the occurrence of an event that may cause potential damage to the party that is the victim of the same and always come with a certain amount of probability or possibility. An uncertainty on the other hand is an event that can occur and cause damage to the system but can never be predicted in advance. Risks can always be measured and hence, there are measures that can be developed to control the same. The risks can be identified and assessed to devise the risk treatment method specific to a particular risk such as risk avoidance or risk mitigation. However, uncertainties cannot be measured and thus cannot be controlled as well (Surbhi, 2016). There is also a key difference between the risk and uncertainty in terms of the impact. Risks will always have a negative impact on the system which may range from low to severe impact. However, uncertainty can have either a positive or a negative impact depending upon the occurrence of the same and the situation as well.
In case of NSW Government, there are a number of risks involved such as data integrity risks, malware threats, operations risks, business risks and many more which have been described above. There can also be a number of uncertainties that may occur that may impact the functioning of NSW Government. A sudden shift in the market that cannot be analyzed or predicted in advance is a common phenomenon. This may have either a positive or a negative impact on NSW Government. There may also be events of natural hazards and disasters. These events may have a serious damage to various components that are involved with the NSW Government.
- Enhanced Disaster Recovery
NSW Digital Information Security Policy (DISP) can proceed successfully with the help of Disaster Recovery strategy. A well planned disaster recovery technique can ensure successful delivery and continuity of the services. These strategies will also ensure that in the time of a disaster, all the information is kept safe and secure well in advance, this strategy will enable the system to be prepared for any of the security attack. A strong back-up plan will also be incorporated in the disaster recovery strategy.
- Network Controls
There are a number of network threats that have been listed above and the same may cause serious damage to NSW Government and its components. Network controls such as time to time network scans along with other mechanisms such authorized network monitoring and advanced intrusion detection systems will enable NSW Government to control as well as mitigate these risks.
- Malware Controls
The list of possible malware that may attack the system is endless. However, there are a number of controls that must be installed to stay protected from such attacks. These controls include installation of anti-virus software, use of enhanced web security and installation of firewall as well.
- Legal and Regulatory Compliance
Adherence to the legal policies and regulatory policies is a must for all the components of NSW Government. The same must be maintained to make sure that the legal risks do not occur. It can be done with the help of a dedicated legal team that will closely monitor all such activities and will also detect any deviation in the path of the same.
- Advanced identity and access management
Access control and identity management is of prime importance to control and mitigate all of the security risks. These include the measures such as use of physical security, Single Sign Offs, Single Sign On, One Time Passwords, strong passwords, unique identification method and many more.
NSW Government as a system is massive in nature and comprises of a number of entities in the form of human factors, machine, processes, interfaces and applications. The same leads to a number of potential security risks such as legal risks, operations risks, business risks, malware threats, network threats, data integrity risks and application vulnerabilities. These risks can have varying degree of impact depending on the category of the information that it affects. There are also a number of uncertainties that are associated with the NSW Government. There are a number of security measures that can be implemented to make sure that the possibility of such events is controlled and the same can be mitigated if occurred. These include a number of network and malware controls, identity management, access management, legal and regulatory compliance along with enhanced disaster recovery plan. There can be issues in the implementation of these security and risk management policies in terms of the human factors, organizational factors and technological factors.
etutorials.org,. (2016). The Four Primary Types of Network Threats :: Chapter 1: Understanding Network Security Threats :: Part I: Introduction to Network Security :: CCSP Cisco Certified Security Professional Certification :: Networking :: eTutorials.org. Etutorials.org. Retrieved 19 August 2016, from https://etutorials.org/Networking/Cisco+Certified+Security+Professional+Certification/Part+I+Introduction+to+Network+Security/Chapter+1+Understanding+Network+Security+Threats/The+Four+Primary+Types+of+Network+Threats/
hubpages.com,. (2016). Different Types of Network Attacks And Security Threats and Counter Measures. HubPages. Retrieved 19 August 2016, from https://hubpages.com/technology/Types-of-Network-Attacks
searchsecurity.techtarget.com,. (2016). Accidental insider threats and four ways to prevent them. SearchSecurity. Retrieved 19 August 2016, from https://searchsecurity.techtarget.com/tip/Accidental-insider-threats-and-four-ways-to-prevent-them
Surbhi, S. (2016). Difference Between Risk and Uncertainty - Key Differences. Key Differences. Retrieved 19 August 2016, from https://keydifferences.com/difference-between-risk-and-uncertainty.html
Vavoulas, N. (2016). A Quantitative Risk Analysis Approach for Deliberate Threats. Retrieved 19 August 2016, from https://cgi.di.uoa.gr/~xenakis/Published/39-CRITIS-2010/CRITIS2010-RiskAnalysisDeliberateThreats.pdf
www.amsro.com.au,. (2016). Information Technology and Security Risk Management Top 12 Risks What are the risks? What are the solutions?. Retrieved 19 August 2016, from https://www.amsro.com.au/amsroresp/wp-content/uploads/2010/12/AMSRO-TOP-12-Information-Technology-Security-Risk-Management-1.pdf
www.finance.nsw.gov.au,. (2016). NSW Government Digital Information Security Policy | NSW ICT STRATEGY. Finance.nsw.gov.au. Retrieved 19 August 2016, from https://www.finance.nsw.gov.au/ict/resources/nsw-government-digital-information-security-policy
www.praxiom.com,. (2016). ISO IEC 27000 2014 Information Security Definitions. Praxiom.com. Retrieved 19 August 2016, from https://www.praxiom.com/iso-27000-definitions.htm
www.us-cert.gov,. (2016). Malware Threats and Mitigation Strategies. Retrieved 19 August 2016, from https://www.us-cert.gov/sites/default/files/publications/malware-threats-mitigation.pdf
To export a reference to this article please select a referencing stye below:
My Assignment Help. (2017). IT Risk Management: NSW Government Comprises Essay.. Retrieved from https://myassignmenthelp.com/free-samples/it-risk-management-nsw-government-comprises.
"IT Risk Management: NSW Government Comprises Essay.." My Assignment Help, 2017, https://myassignmenthelp.com/free-samples/it-risk-management-nsw-government-comprises.
My Assignment Help (2017) IT Risk Management: NSW Government Comprises Essay. [Online]. Available from: https://myassignmenthelp.com/free-samples/it-risk-management-nsw-government-comprises
[Accessed 04 April 2025].
My Assignment Help. 'IT Risk Management: NSW Government Comprises Essay.' (My Assignment Help, 2017) <https://myassignmenthelp.com/free-samples/it-risk-management-nsw-government-comprises> accessed 04 April 2025.
My Assignment Help. IT Risk Management: NSW Government Comprises Essay. [Internet]. My Assignment Help. 2017 [cited 04 April 2025]. Available from: https://myassignmenthelp.com/free-samples/it-risk-management-nsw-government-comprises.
