Digital Forensic Methodologies
Question:
As part of the auditing team in capacity of a Digital Forensics expert, your task is to prepare digital forensics investigative plan to enable a systematic collection of evidence and subsequent forensic analysis of the electronic and digital data. Assuming all systems are Windows based, this plan should detail following:
- justify why use of the digital forensic methodology and approach is warranted including procedures for corporate investigation.
- describe the resources required to conduct a digital forensic investigation, including team member skill sets and required tools.
- outline an approach for data/evidence identification and acquisition that would occur in order to prepare the auditors for review of the digital evidence.
- outline an approach and steps to be taken during the analysis phase making the assumption the computer system is a Microsoft Windows-based computer.
Abstract
Information technology has become integral part of the human life, no matter of the age. And businesses have exploited the information technology to a great extent that every business activity is automated to decrease the time and increase the productivity. Though it is a good and encouraging aspect with the IT, the cyber crimes are also increasing at the same pace. So, the companies have to emphasize on the security of the intellectual information as the companies do for the automation through the information technology. Global Finance company has materialized its vision of globalization through information technology and faced the challenge of the compromise of the system. The digital forensic investigation team can encounter such challenges to find the sources of the compromise and secure the systems and network back with necessary safety standards.
Introduction
Global Finance company is one of the huge companies in Australia, with wide range of finance products and wide range of customers, throughout the world. The company has enabled the information technology with necessary infrastructure in the head office and all of its child organizations. A suspect of compromise has been detected from the manager’s computer from the Queensland branch, which is one of its child organizations. The investigation audit team is formed to investigate the source of the compromise. The team has been deployed in the branch office to conduct the digital forensic investigation.
Global Finance is the company that needs the digital forensic investigation done by the audit team. The case study includes the following important points about the company.
- Global Finance Company is located in Australia and its branches are spread all over the world.
- It has over 10,000 employees throughout the world.
- The company stands to be an international player in global finance market.
- The company provides investment, superannuation and retirement services to the clients. The clients include right from individuals to larger corporate.
- The company has the expert employees in global shares, property, private equity, fixed interest and credit.
- An information security concern has been raised from a branch office to the information security office in the head office.
- Global Finance facilitated its global business with the support of the information technology.
- After year 2000, regular updates for application infrastructure and network infrastructure starts missing in the child organizations.
- The access among the child organizations is flat and relatively less secured. So, the users from one child organization can access the data from the servers and workstations from any other child organizations.
- One of the branch managers from Brisbane branch felt compromise in his computer.
- Both the servers and workstations from all the offices are based on Microsoft Windows.
- The firewalls and network segmentation are poorly implemented.
- Though intrusion detection and logging exist in the branches, these are hardly used.
- Head office consists of enough infrastructure for the investigative and forensic capabilities.
- An auditor team has been formed to conduct a digital forensic investigation in the branch office, where the suspect has been felt.
- The team has the responsibilities of both reviewing paper based documents as well as digital forensic analysis, by finding the digital evidences from all the files like MS-Word, Spreadsheet, deleted files and Outlook.
Digital forensic methodology is preferred to be processed or executed by the information security office. It is because all the other methodologies, like computer forensic, mobile forensic, network forensic and data recovery can give partial investigation results rather than complete investigation of the source of the compromise, as these are all the sub branches of the digital forensic.
Digital forensic investigation conducted for the regional office of the Global Finance Company has the following scopes.
- Security lap identification from the network of the regional office
- Malicious activities identification with details of who, what, why, when and where
- Legal procedure identification, if the cyber crime is illegal
- Identifying the impact of the compromised manager’s computer, if there is any compromise
Digital Forensic Investigation Approach
The audit team of the Global Finance Company can follow Four Step Forensics Process or FSFP. This digital forensic investigation model stands to be a most effective model for investigation of the compromise happened in the regional branch of the Global Finance Company.
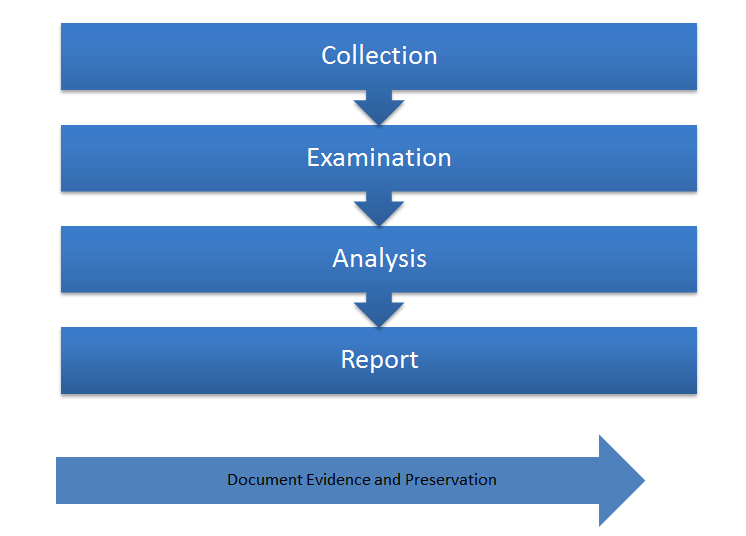
Digital forensic investigation needs a lot of resources to successfully process and create a report for the same. It demands technological support with the tools, techniques to implement the processes as well as it demands the expertise of the audit team in multiple dimensions.
Digital forensic methodologies that can be implemented are static methodologies and dynamic methodologies. Various tools, like EnCase, ProDiscover and many other tools are needed to conduct thorough check on the existing network system present in the branch office.
ACPO Guidelines
ACPO or Association of Chief Police Officers is the standard guideline set consisting of four principles. When the computer or digital forensic investigation is conducted, the audit team has to follow the following principles.
Principle 1: The data present and collected from the targeted computers are to be preserved as is, without performing any alterations or changes.
Principle 2: The data collected must be well preserved safely, so the audit team must have enough expertise and should be enough competent to handle the collected data safely, and whenever it is required, the course of action during the processes must be explained with necessary evidences.
Principle 3: All the documentation and audit trails must be created clearly and should be preserved. When the third party executes the process, the same results are expected.
Principle 4: Each and every team member of the audit team should be responsible for the entire investigation conducted.
The audit team members should posses enough expertise in the core level operating system, networking system and the necessary tools and techniques needed to use for the investigation. The skill set must be extended to the multiple dimensions, like cyber crime knowledge, legal procedures and many related to the same.
- The impact of the investigation must be known prior to the initiation of the investigation, in terms of affected productivity, because of the down time, etc.
- All information from the manager’s workstation, servers and other workstations must be collected.
- Obtain all the important network information
- Identify the storage content, both internal and external devices
- Forensic tools that are applicable and to be used for the investigation are to be listed and made available for usage.
- Each and every activity must be well documented during the course of investigation
- Target computer forensic imaging has to be done and then hashed to check the integrity of the data
- Live network traffic has to be captured
Digital evidences must be collected from the workstations of the managers, others and the servers present in the regional office. The following evidences are useful.
- IP addresses
- System Log files
- Windows registry information
- Network topology and diagrams
- Network information that consists of hubs, routers, network topology documentation, switches, servers, network diagrams and firewalls
- Information from both the internal storage and external storage devices, like CD, flash drive, DVD, USB drive, remote computers, portable hard disc and memory card.
Digital evidence collection: Digital evidence acquisition in the regional branch of the Global Finance company has to be done in two stages.
Volatile memory is the temporary memory, for which the data is held, only while the workstation or server is working. Primarily volatile memory is RAM. Same LAN must be accessed to access the manager’s computer to acquire this data.
Give the command, cryptcat 6543 –k key
Computer data can now be acquired with the command,
cryptcat -1 –p 6543 –k key >>
In addition to these commands, graphic user interface tools, like Tcpview, Rootkit Revealer and Process Explorer would be helpful to the team to retrieve the volatile data like, system data, time, logged user, open ports, running processes and network connections.
There are many other tools used for Windows based systems for volatile data capture are,
netusers and qusers, netfile,HBGra’s F-Response, ipconfig, HBGray’s FastDump, doskey, to identify all the network traffic towards the manager’s computer.
The clipboard content which is potential digital evidence is also collected by the team.
Permanent memory or non volatile memory stands significant source for the digital forensic investigation. Permanent data is collected through both online and offline methods.
Offline data is collected from the hard drive duplicator tools, such as FTK imager, Guymager, DCFLdd, IXimager and EnCase are used to collect the data from the hard drives of the manager’s workstation, other workstations and the servers. Other permanent storage devices like CD, DVD, memory cards, flash drives, pen drives and other drives are also collected from the office.
Online data, like firewall logs, antivirus logs and domain controller logs is collected with the help of tools like ethereal and Wireshark tools.
Once all the potential digital forensic evidences are collected, detailed examination is done by comparing the original and logical copies collected and checked for any hypothesis and deviations. Such examinations can give clues of how the manager’s computer is compromised.
Detailed examination is done for windows registry, network forensic, file system and database forensic. The team uses the following commands for the same.
c:echo text_mess > file1.txt:file2.txt
the above file is then retrieved through the command,
c:more <file1.txt:file2.txt
windows registry examination is done with the following hives and structures present in it,
- HKEY_USERS
- HKEY_CURRENT_USER
- HKEY_CURRENT_CONFIG
- HKEY_CLASSES_ROOT
- HKEY_LOCAL_MACHINE
Network forensic is enabled using the tools and techniques so that the following potential information can be accessed from the manager’s computer.
- System information
- Service listings
- Process listings
- Registry information
- Network connections
- Registered and Logged on users
- Binary dump of memory
The above information can be accessed with the network forensic tools, NetStumbler, TCPDumpWindump, Wireshark, Sleuth Kit and Argus.
Many tools and methodologies are used by the audit team to analyze the collected and examined evidences. Analysis is done according to the following.
- Keyword searches in all the files
- Recovering the deleted files
- Registry information extraction from the workstation of the manager and other systems.
The tools used in this phase for the team are EnCase, FTK and ILOOKIX. These tools are helpful to recover the internet documents, chat logs, emails, images, internet history, accessible and deleted space from the manager’s computer and cache files of OS. Hash signature forensic tool helps to find notable files. When SSD drives are present in the systems, even after secure erase operations also the data can be recovered.
Once the analysis is done by the team, it extracts the answers for the following objectives.
- Opportunities for reconstruction of the events
- Accountability of the users and administrators
- Detection of the attempts violation
- Providing information of identification of the problems
The final report is generated by the audit team, with all the documented information.
Final Report
|
Purpose of the Report |
Digital Forensic Investigation conducted on the compromise of the manager’s computer in a regional office of the Global Finance Company |
|
Author of the Report |
The audit team |
|
Incident Summary |
The sources of compromise are x, y, z reasons |
|
Evidences |
All the effected files, registry data, log data |
|
Analysis |
All the analyzed data from the analysis part |
|
Conclusion |
All the digital evidences are extracted and the sources of compromise are found |
|
Documents to Support |
Volatile and non- volatile data, tool generating info, log info and registry info and so on. |
Conclusion
The source of compromise of the manager’s computer in the regional branch of Global Finance Company is found through digital forensic investigation.
References
- “Cyber Forensic Investigation Plan”, International Journal of Advance Research (2008), UOAR.org, Volume 1
- Siti Rahayu Selamat, Robiah Yusof, Shahrin Sahib (2008), “Mapping Process of Digital Forensic Investigation Framework”, JCSNS International Journal of Computer Science and Network Securit, Vol 8.
- Kenneth J. Zahn (2013), “Case Study: 2012 DC3 Digital Forensic Challenge Basic Malware Analysis Exercise”, GIAC (FREM) Gold Certification
- John Ashcroft (2001), “Electronic Crime Scene Investigation, A guide for First Responders”, NIJ Guide
- M Reith, C Carr, G Gunsch (2002). "An examination of digital forensic models". International Journal of Digital Evidence
- Richard Brian Adams (2012), “The Advanced Data Acquisition Model (ADAM): A Process Model for Digital Forensic Practice”
- Agarwal, A., Gupta, M., Gupta, S., & Gupta, S. C. (2011). “Systematic Digital Forensic Investigation Model”, International Journal of Computer Science and Security, 5(1), 118-130.
- Armstrong, C. (2003), “Mastering Computer Forensics. In C. Irvine & H. Armstrong”, Security Education and Critical Infrastructures Kluwer Academic Publishers.
- Aquilina, M.J., (2003), “Malware Forensics, Investigating and Analyzing Malicious Code”, Syngress,
- Carvey, H., (2005), “Windows Forensics and Incident Recovery”, Boston: Pearson Education Inc.
To export a reference to this article please select a referencing stye below:
My Assignment Help. (2016). Digital Forensics Investigative Plan For Global Finance Company Essay.. Retrieved from https://myassignmenthelp.com/free-samples/the-case-a-digital-forensic-investigation-plan.
"Digital Forensics Investigative Plan For Global Finance Company Essay.." My Assignment Help, 2016, https://myassignmenthelp.com/free-samples/the-case-a-digital-forensic-investigation-plan.
My Assignment Help (2016) Digital Forensics Investigative Plan For Global Finance Company Essay. [Online]. Available from: https://myassignmenthelp.com/free-samples/the-case-a-digital-forensic-investigation-plan
[Accessed 26 May 2025].
My Assignment Help. 'Digital Forensics Investigative Plan For Global Finance Company Essay.' (My Assignment Help, 2016) <https://myassignmenthelp.com/free-samples/the-case-a-digital-forensic-investigation-plan> accessed 26 May 2025.
My Assignment Help. Digital Forensics Investigative Plan For Global Finance Company Essay. [Internet]. My Assignment Help. 2016 [cited 26 May 2025]. Available from: https://myassignmenthelp.com/free-samples/the-case-a-digital-forensic-investigation-plan.
