ELECTRONSRUS is a company that designs, manufactures and sells electronic network equipment based in Wrexham. Business is so good for this HI-TEC company that they have decided to take over the old hospital which is on the other side of Wrexham about 5 miles away from their existing building. The buildings require some modification to fit in with the new plans of the company and as part of this you have been asked to provide a design to install the network infrastructure
To ensure that they do not interfere with the support of their customers during the move they have decided to install a new IT system and Computer Network in the new building before they move in. For this reason, and for the immediate future, a link to the old office will be essential.
The attached sheet shows a plan of the premises. A list of the proposed use of the buildings is provided below. Further information is available from your lecturer.
1. Brief but concise description of the available technological solutions
2. Compare and contrast these options
3. Make a judgement as to the preferred solution for ELECTRONSRUS, justifying your choice.
ELECTRONSRUS are manufacturers of electronic network equipment’s. They design &sale their products in Wrexham,United Kingdom since long years. Because of increased business, they have expanded to include new office buildings in their company.
ELECTRONSRUS hire us, for the effective and vital communication between old and new offices and within the premises of each building.We are providing Virtual local area network (VLAN) for the whole ELECTRONSRUS Company.
VLAN is a virtual LAN.Say , you have connected multiple PCs to a single switch providing a private subset of LAN where computers are interacting with each other.A single switch will behave like multiple switches .Each VLAN has its own boradcast domain and IP subnet.[1]
The VLAN is used to create multiple broadcast domains in a switch. For example a single CISCO catalyst switch 2970 series of 48 ports can be divided in two VLANs . VLAN 1 is craeted using 1 to 24 and VLAN 2 is created using 25to 48 .One of the special feature of VLAN technology is less hardware usage like two VLANs are created on a single switch .VLANs help in minimising traffic.To connect VLANs in network that have multiple interconnected switches, we use VLAN trunking. Cisco catalyst 2970 supports two different trunking protocols: Inter – Switch Link (ISL) and IEEE 802.1q.VLAN provides physical topology independence by grouping users regardless of their physical location. For instance,a two storey building with 20 users on each floor is connected via CISCO catalyst 2970 switch with 48 ports. VLAN is bounded in logical subnet so to reach other subnet layer 3 routers are needed. All devices in same VLAN share same IP subnet and PCs connected in different VLANs are in different subnets. It helps in reducing latency by using Layer 2 devices and therefore, minimizing usage of layer 3 routers.VLAN technology is beneficial in existing practical networks.There can be port based VLAN , Mac address based VLAN and Layer -3 based VLAN.IEEE 802.1Q is a standard for VLAN and provides details of VLAN interoperions.IEEE 802.1 Q has provided standard method for implementation in Ethernet frames.
- Effective & easy management of workstations
- Load Balancing
- Bandwidth Allocation
- Effective Securitymanagement and more security options
- Increased performance
- Simplified software configurations
- Reduced latency
VLAN
VLANs provide an easy and cheap costs infrastructure for networks. They allow easy management of large networks by enabling centralized configuration of devices. They give high performance over shared devices by reducing collisions and limiting broadcast traffic. It simplifies configuration by grouping of department resources into a single subnet. IP addresses and subnet masks configured on PCs will be in same subnet for same VLAN.

Figure 1:Network diagram for VLAN configuration
- Installation of IT system and computer network in new building.
- All admin,design, manufacturing plant and store should be connectedto reliable network.
- A network link must be provided to connect old and new offices of ELECTRONSUS.

Figure 2 :New site for ELECTRONSRUS
Site Description:
Administration office: The administration office is a threestorey building and is going to be used for various departments.
Top Floor => Management and directors sittings.
Total member at floor = 60 members
Middle Floor => Human resource & purchasing department personnel’s
Total member at floor = 60 members
Ground Floor => IT Staff
Total member at floor = 60 members
Design office: This is a 2storey building and is going to be usedin various departments.
Top Floor => Engineering design staff
Total member at floor = 150members
Ground Floor => Sales & Marketing
Total member at floor = 75 members
Stores office: The Stores is where all the components for the manufacturing are kept along with the completed equipment ready for dispatching. It is a fourstorey building with approximately five members of staff on each floor.
Top Floor => Store Staff
Total member at floor = 5 members
Second Floor => Store Staff
Total member at floor = 5 members
First Floor => Store Staff
Total member at floor = 5 members
Ground Floor => Store Staff
Total member at floor = 5 members
Manufacturing Plant: This is where the equipment is manufactured. It is a single storey building where about 120 production operatives will work. They are many different areas in this building since there are lots of different tasks that need to be performed. It includes a Machine shop where there are heavy electrical cutting machines and Arc welders. There is also a test bay where all the equipment is thoroughly tested before being shipped. The offices are for the Area managers.
It must be possible to have the following External access:-
- General Internet access
- Access to Suppliers Network
- Access to Suppliers to restricted part of ELECTRONSRUS Intranet
- Access for Sales & Marketing staff to the ELECTRONSRUS Intranet when they are remote from the site
The most mainstream designs, or topologies, incorporate the token ring, bus, point to point, star topologies.
With a bus design, every node/hub is joined consecutively along the system backbone. A node/hub is any equipment associated with the system, for example, a printer, scanner or PC. Backbone is the term used to portray the primary links to which the system fragments are joined. At the point when one node/hub sends data to another node/hub through the system, the data goes along the backbone until it achieves the wanted accepting node/hub.
Benefits Of VLAN

With a ring arrangement, every node/hub is joined successively along the system backbone. Be that as it may, not at all like the bus arrangement, the end of the network associate with the first node/hub, resulting in a circuit. Node/hubs on a token ring alternate sending and getting data. In the token ring topology, a token goes along the backbone with the data being sent. The node/hub with the token sends data to the following node/hub along the backbone. The getting node/hub peruses the data tended to it and afterward passes the token and any extra data to the following node/hub. This proceeds until the token and information make it back to the first node/hub in the system.

With a star design, every node/hub is joined with a focal center point by means of system sections. At the point when one node/hub sends data to another node/hub, the data goes through the hub. The hub does not channel or course the data in any capacity; it just serves as a connector between system sections.

Point-to-point topology is the least complex of all the system topologies. The system comprises of an immediate connection between two PCs. This is quicker and more solid than different sorts of associations since there is an immediate association. The impediment is that it must be utilized for little zones where PCs are in close vicinity.
A VLAN is a switched network that is segmented logically by departments of an organization or applications. A VLAN creates broadcast domain defined set of switches. VLAN consists of end systems, switches, and routers. VLANs are created to provide the segmentation services.It address scalability, security and network management. Routers in VLAN topologies provide broadcast filtering, security, address summarization& traffic flow management. [4]
VLANs technology divides broadcast domains in different VLANs. So that packets are switched between ports designated to the VLAN range.
Cisco IOS software (switches and router OS) provides full-feature routing at Layer 3 and translation at Layer 2 between VLAN.Five protocol are mainly used: [4]
- IEEE 802.10 Protocol
- IEEE 802.1Q protocol
- Inter – Switch LinkProtocol
- ATM LANE Protocol
- ATM LANE Fast Simple Server Replication Protocol
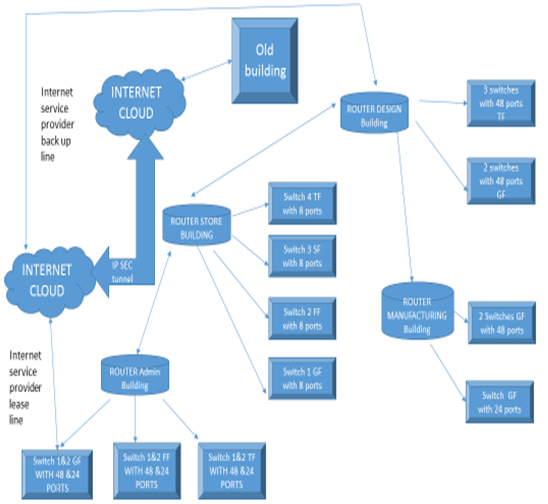
Admin office, manufacturing, store and design office routers are connected. Admin office is connected via the internet cloud, and its fixed line will be leased theline by the service provider. To connect old building/office ip sec tunnel is used.
Design building router is used for back up lease line by service provider.
Multiple switches are used in topology with 48, 24 0r 8 ports. There will be free ports in every vlan , so that in the future there can be enhancements.
|
New Buildings premises |
Floor |
Members |
IP address Subnet |
IP address range |
Name of the Vlan |
|
First |
60 |
192.168.0.0/26 |
192.168.0.0- 192.168.0.62 |
Vlan_admin_First |
|
|
Second |
60 |
192.168.1.0/26 |
192.168.1.0- 192.168.1.62 |
Vlan_admin_Second |
|
|
Third |
60 |
192.168.2.0/26 |
192.168.2.0- 192.168.2.62 |
Vlan_admin_Third |
|
|
Design Building |
|||||
|
Engineering design |
Top |
150 |
192.168.5.0/25 |
192.168.5.1-192.168.5.126 |
Vlan_design_Top |
|
Sales and Marketing |
Ground |
75 |
192.168.5.128/25 |
192.168.5.129- 192.168.5.254 |
Vlan_design_Ground |
|
Stores building |
|||||
|
First |
5 |
192.168.7.0/28 |
192.168.7.1-192.168.7.14 |
Vlan_Stores_First |
|
|
Second |
5 |
192.168.8.0/28 |
192.168.8.1-192.168.8.14 |
Vlan_Stores_Second |
|
|
Third |
5 |
192.168.9.0/28 |
192.168.9.1-192.168.9.14 |
Vlan_Stores_Third |
|
|
Manufacturing Plant |
Ground |
120 |
192.168.10.0/25 |
192.168.10.1-192.168.10.126 |
Vlan_manf_Ground |
Customer Requirements
At the point when Ethernet was initially implemented, a great many people utilized a copper coaxial link. Notwithstanding, the most extreme length of this link was 500 meters, which was not sufficiently long for a few systems. To address this issue, system designers utilized repeaters to join a few Ethernet portions.
Bridges give a Transparent ways to joining LANs. A bridge is a gadget that join physically isolated LAN fragments, (for example, diverse Ethernet links) into one legitimate LAN section. There are four classifications of bridges: source routing, Transparent, translating, and encapsulating.
Transparent extensions are utilized for Ethernet, though source routing bridges are utilized for token ring systems. Encapsulating extensions unite two fragments of the same media, (for example, token ring to token ring) more than a medium. The accepting extension takes out the envelope, checks the destination, and sends the casing to the destination gadget.
LAN fragments joined by a switch are physically and intelligently separate systems. Rather than a bridge, when different system sections are joined by a switch they keep up their different legitimate identities (system location space), yet constitute an internetwork.
Switches determine the destination and course for every bundle, and they can be utilized to direct bundles and interconnect a mixed bag of system architectures. A noteworthy contrast between an extension and a switch is that the bridge recognizes bundles by source and destination address, though a switch can likewise recognize parcels by convention sort. Switches accommodate the interfaces to WANs.
Ethernet communicates over the system utilizing the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) process. A convention utilizing CSMA/CD screens, or listens to, the media for system movement, or data going through the system starting with one hub then onto the next. In the event that a hub does not sense any activity, it will send casings or bundles of data onto the media. A system edge is similar to a sent letter. The letter is put in an envelope that has an arrival location and the location of its destination. Information are similar to the letter and the casing is similar to the envelope. The information is put in the edge and the casing has the tending to data and lapse checking code
There are many vendors of network devices like Allied Telesis, Arista , Avaya , Brocade , Cisco , Dell , D-Link ,Draytek , Enterasys Secure Networks , Extreme Networks ,Fortinet, HP, Juniper Networks ,Net gear , Transition Networks and Zyxel.
Site Map And Details
But, CISCO is one of the leaders in networking solutions and provides a wide variety of switches from SMB to enterprise and ISP provider networks.Cisco peripherals are alittle bit costly, but they are known in themarket for their customer support. We are opting for Cisco peripherals.
Ideally thenetwork should be designed hierarchically in 3 layers (Access, Aggregation, and Core) but looking at the requirements I am proposing following guidelines:
Each building will have its layer twoswitches where they do would be isolated using VLANS. Vlanbe restricted Broadcast domain. We will call It as Access Layer
Private IPv4 Subnets would be assigned based on number of members per floor. We can go for IPv6 addressing, but that would make the migration cumbersome as of now.
We can plan for Migration to IPV6 if required once everyone is migrated to anew network
Aggregate traffic of these switches will be uplink to Core/Aggregate router that in our case would be one.
Each building would be connected to each other using Core router
We can have redundancy by having multiple Core routers as well Layer 2 Switch, but this would depend on customer investment and criticality both of which is still unclear.
Leased line would be purchased from Service provider and will be connected to any building core router that would act as a gateway.
We can have back up leased line as well from other service provider, but that would again depend on customer BCP.
Core router would be required to do NATTING in case of IPV4 address to access the internet as private range is not routable on internet
VLANs are available on the CISCO Catalyst 6000 running CatOS 5.4 or later, on the Catalyst 4000, 2980G, 2980G-A, 2948G, and 4912G running CatOS 6.2 or later.
We are opting for CISCO Catalyst 2970 series. CISCO catalyst is layer 2 Series Switch used for Access connectivity in VLANs. I am selecting Cisco hardware as Cisco is known for its customer support as well as they keep bringing latest features on their products as and when required. These series switches have features like QOS, STP, etc. which can be required in the network as anetwork grows. There are vendors Like Alcatel Lucent, Summit, Juniper that offer similar hardware required for the network, but I am going in with Cisco Hardware.

The following two configurations comprise the Cisco Catalyst 2970 Series:
- Cisco Catalyst 2970G-24TS-24 Ethernet 10/100/1000 ports and four small form-factor pluggable (SFP) ports
- Cisco Catalyst2970G-24T-24Ethernet 10/100/1000 ports
Cisco catalyst 2970m series comes with Cisco Enhanced Image (EI) IOS ® Software .CISCO catalyst suports IGMP leave timer ,IGMP snooping querier,DSCP transparency , VLAN-based QoS1 and hierarchical policy maps on SVIs , Device Manager ,SSL Version 3.0,IEEE 802.1x, Flex Links , SFP module diagnostic management ,Smart ports Macros. [3]
- Cisco catalyst 2970 series switches around 15 or more
- Router 2900 series around 3 in quantity.
- Connectors and cables
- 10BASE-T ports: RJ-45 connectors , 100BASE-TX ports: RJ-45 connectors
- 1000BASE-T ports: RJ-45 connectors,
- 1000BASE-T SFP-based ports: RJ-45 connectors[3]
- 100BASE-TX ports: RJ-45 connectors
- 2-pair Category 3, 4, or 5 unshielded twisted-pair (UTP) cabling
- 2-pair Category 5 UTP cabling
- 1000BASE-SX, -LX/LH, -ZX, and CWDM SFP-based ports: LC fiber connectors (single-mode or multimode fiber)[3]
- Management console port: RJ-45-to-DB9 cable for PC connections[3]
- Power connector RPS 675
- Internal power supply connector
- Environmental conditions
- Operating temperature:32 to 113ºF (0 to 45ºC)[3]
- Storage temperature: -13 to 158ºF (-25 to 70ºC)[3]
- Operating relative humidity: 10 to 85 percent (noncondensing)[3]
- Operating altitude: Up to 10,000 ft (3049 m)[3]
- Storage altitude: Up to 15,000 ft (4573 m) [3]
- Contempora – 4(C4) Series Rack cabinet system
- Linux windows servers
- For VOIP Connectivity , require IP phones
- For Security , surveillance cameras(CCTV)
- Biometrics , card punching system
- Centralized Air conditioning
External Access

As the name suggest LAN operating system is required to operate on the LAN system, manage the tremendous work load with a number of various types of server attached to it. It has basically two aspects (i) Server Software (ii) Work station Software. As case of other multi user operating system, LAN operating system also facilitate the sharing of expensive resources such as printer, storage space etc. among all LAN users, provides security of data permits connections to other network.
There are various types of LAN operating systems for example Novel Netware, LAN server, omni met, PC Net, IBM PC LAN, Etherlik plus etc.
- Catalyst 2970 G-24T uses Cisco IOS Release 12.2(18)SE
- Catalyst 2970 G-24TS uses Cisco IOS Release 12.2(18)SE
- Supported windows 98,NT 4.0 , 2000 XP & 7
- Supported Microsoft internet explorer 5.5,6.0,7.0.
- Supported Microsoft Netscape Navigator 7.1
- 2970 Supports IGMP leave timer ,IGMP snooping querier,DSCP transparency , VLAN-based QoS1and hierarchical policy maps on SVIs , Device Manager ,SSL Version 3.0,IEEE 802.1x, Flex Links , SFP module diagnostic management ,Smartports Macros.
- Cisco IOS software release 15.0.
All the above requirements, can be altered after any discussion with IT Team of ELECTRONSRUS.
Internet connection or broadband can be taken from any SERVICE PROVIDER like reliance,airtel, Vodafone etc.
I suggest following connections:
BroadBand Connections: It is a high speed internet connection. User can dial phone and remain connected on internet at the same time.With broadband , users can watch live news and sports.
Fixed Broadband Connections: There is wireless or fixed modem in this connection.
Fixed Wireless and satellite connections: In some countries, in remote areas fixed wireless connection or a satellite connections are provided.
Remote Procedure Call (RPC) is an authoritative method for building applications like client/server based, distributed etc.
The Remote Procedure Calls (RPC) method is a model of high-level interactions for various applications in the network. RPC is a dominant method for building applications based on client/server or distributed networks. It is base on enlarging the idea of predictable or local calling procedure, in such a way that the procedure called not required to exist near the similar address space just like the procedure of calling. The two procedures can be on the same system, or rather can have dissimilar systems and are connected using a network.
By means of RPC, agenda on platform of networking can interact with resources like remote and local. RPC permits the use of particular kinds of calling procedures that are designed to conceal the underlying mechanisms on which network is working in a network application. The complication concerned in the expansion of distributed doling out is decreased by maintaining the remote call semantics whether the same or different the server and client are using the same system.
This feature of transport autonomy of RPC cuts off the elements of physical and logical layer application from the layer of data communications method and gives the flexibility to the application for a diversity of transports applications.
Remote procedure call (RPC), exactly, permits you to call up a course of action on both a local and a remote machine evidently. A call of client is interpreted into a remote machine call
Remote File SystemàWrite (“hello”);
File SystemàWrite (“Hello”);
RPC is executed on above layer of two-way messaging by means of a procedure stubs available on the client as well as server. The procedure stubs just offers the interface of invocation for programmers. The real applications of those actions are described remotely.
Basically the client stub has following tasks at hand:- Marshalling or Building messages
- Sending messages
- Response wait
- Unpack reply
- Return result
The server stub has following tasks at hand:
- Do N threading in order to wait for the requests
- Loop:
- For some time just look for command
- Upon receiving command perform decoding and unpacking of request parameters, this is also called as unmarshalling
- Now next step is procedure call
- Using results obtained build message for replay
- Now finally send reply
The stubs are repeatedly produced. A client has no clue about which port is for communication because this is runtime. Consequently, the client requests to have an already known port for moreover a server or a process name server that decides which server to get in touch with.
- RPC acts as a local host but Mask remote function calls
- The RPC is a Client-server based model
- message passing is the basic way for Request to reply paradigm in remote procedure call
- Functions uses methods like message passing and using function parameters it returns value
- The Remote procedure call do function call based on the pattern of Language-level
- The Remote procedure call is quite simple for any programmer to understand
- There is a Synchronous method for request and reply communication between host and client
- It has no specific choice for any programming language and hence language neutral
- Before forwarding a reply to any request, it do matches the corresponding port for that requests
- There is automatic matching for replies and requests
- It posses Distribution transparency which put out of sight the complication of a distributed system and gives quality assurance
Sometimes there can be failure in the system due to semantics of Invocation hold up by RPC due to some congestion in network or server, congestion in client network or last due to server failure
- One disadvantage is the way of interaction that is it uses Synchronous interaction for the request and replies hence more chance of connection loss etc.
- Client and server are closely coupled and have direct effect on each other. In some scenarios the client might block the process for a quite long time in case loading of server directs to client with multi-threaded programming
- Some clients are slow or failed to reply due to network problem or other which delays the reply to the server
- There must be multi-threading at the server interface because generally it has more than 1 client
- Distribution Transparency is not probable to mask all troubles
- RPC model is not object-oriented and hence duplication cannot be avoided
- The above factor leads to invocation of server’s functions rather than using objects to call methods, which just store references and hence avoid all loading at invocation.

Through IP sec tunnel old and new office buildings are connected.
IP SEC TUNNEL MODE
IPSec tunnel mode is the default mode. With tunnel mode, the entire original IP packet is protected by IPSec. This means IPSec wraps the original packet, encrypts it, adds a new IP header and sends it to the other side of the VPN tunnel (IPSec peer).[5]
Tunnel mode is most commonly used between gateways (Cisco routers or ASA firewalls), or at an end-station to a gateway, the gateway acting as a proxy for the hosts behind it.[5]

Information and computer security is a task of software team. We concern here for physical security.
Physical security faces different threats of environment, political, natural as compared to computer and information security. The threats are classified as:
- Natural Calamity threats: Catastrophe, Floods, earthquakes, storms and tornadoes, fires, extreme temperature conditions and so forth.
- System threats:Power supply issues, voltage issues, temperature issues & so forth.
- Man interference threats: Unauthorized access, hijack attack, spoof attack & so on.
- Politically motivated threats:Strikes and riots in the city, civil disobedienceand so forth.
- Develop security team.
- Develop proper plan.
- Do risk analysis management.
- Entries in critical data center rooms should be limited
- Proper pathways around building to guide to main entrance
- Back door entries should be limited to suppliers and equipment deliveries.
- Pathways should have proper lighting to guide people in night.
- Do natural surveillance sometimes
- Deploy electronic motion sensors
- There should be continuous video surveillance
- Biometric access and exit sensors for critical areas like data center
- UPS backup generators ,gas based fire suppression system
- Server monitoring
- Redundant HVAC controlled environments
- Proper fencing
- IP support for devices such as switches and routers
- Effective Fencing near building
- Proper web access management
- Proper password management on devices
- Back up of data every day.
- “Difference between VLAN and LAN”.[online]. Available:https://www.differencebetween.net/technology/internet/difference-between-vlan-and-lan/.[Accessed: July 19, 2011].
- “Vlan configuration examples”[online]. Available:https://www.h3c.com/portal/Technical_Support___Documents/Technical_Documents/Switches/H3C_S3100_Series_Switches/Configuration/Typical_Configuration_Example/Low-end_E_S_Configuration_Examples(V1.04)/200809/616200_1285_0.htm.
- “Cisco catalyst 2970 series switches”[online]. Available: https://www.cisco.com/c/en/us/products/collateral/switches/catalyst-2970-series-switches/product_data_sheet09186a0080197384.html.
- “Routing between VLANs overview”[online]. Available:https://www.cisco.com/en/US/docs/ios/lanswitch/configuration/guide/lsw_rtng_vlan_ovw_ps6350_TSD_Products_Configuration_Guide_Chapter.html
- “Understanding VPN IPSEC TUNNEL mode and IPSEC TRANSPORT MODE”[online]. Available: https://www.firewall.cx/networking-topics/protocols/870-ipsec-modes.html
To export a reference to this article please select a referencing stye below:
My Assignment Help. (2017). Designing Network Infrastructure For ELECTRONSRUS - VLAN Technology Essay.. Retrieved from https://myassignmenthelp.com/free-samples/electronsrus-management.
"Designing Network Infrastructure For ELECTRONSRUS - VLAN Technology Essay.." My Assignment Help, 2017, https://myassignmenthelp.com/free-samples/electronsrus-management.
My Assignment Help (2017) Designing Network Infrastructure For ELECTRONSRUS - VLAN Technology Essay. [Online]. Available from: https://myassignmenthelp.com/free-samples/electronsrus-management
[Accessed 09 May 2025].
My Assignment Help. 'Designing Network Infrastructure For ELECTRONSRUS - VLAN Technology Essay.' (My Assignment Help, 2017) <https://myassignmenthelp.com/free-samples/electronsrus-management> accessed 09 May 2025.
My Assignment Help. Designing Network Infrastructure For ELECTRONSRUS - VLAN Technology Essay. [Internet]. My Assignment Help. 2017 [cited 09 May 2025]. Available from: https://myassignmenthelp.com/free-samples/electronsrus-management.
